Exam 2
1, add if you have time
10. The separation of network infrastructure from the control layer, combined with the ability to centrally program a network design in a vendor-neutral, standards-based implementation, is an example of what important concept?
A. MPLS, a way to replace long network addresses with shorter labels and support a wide range of protocols
MPLS (Multiprotocol Label Switching) is indeed a way to replace long network addresses with shorter labels, and it supports multiple protocols. However, it does not involve separation of the network infrastructure from the control layer in the way described in the question.
B. FCoE, a converged protocol that allows common applications over Ethernet
FCoE (Fibre Channel over Ethernet) is a protocol that allows Fibre Channel communications to run directly over Ethernet. It is primarily used in storage area networks and does not align with the description provided in the question.
C. SDN, a converged protocol that allows network virtualization
CDN (Content Delivery Network) is a system of distributed servers that deliver content, especially web content, to users based on their geographic location. This concept is not related to the central programming of a network or the separation of network infrastructure from its control layer.
D. CDN, a converged protocol that makes common network designs accessible
This is a primary feature of Software-Defined Networking (SDN). SDN decouples the control plane (which decides how to handle network traffic) from the data plane (which actually handles the traffic) allowing for centralized network management and programming.
12. Susan is worried about a complex change and wants to ensure that the organization can recover if the change does not go as planned. What should she require in her role on the organization's change advisory board (CAB)?
A. She should reject the change due to risk.
Simply rejecting a change due to potential risk without further analysis or mitigations isn't an appropriate approach. The CISSP emphasizes the importance of risk assessment and implementing controls to mitigate those risks, rather than avoidance.
B. She should require a second change review.
While a second review can be helpful in some circumstances, it doesn't directly address the concern of recovering if the change fails. The CISSP emphasizes the importance of recovery strategies and planning, rather than just additional reviews.
C. She should ensure a backout plan exists.
This is a key principle in change management. If a change doesn't go as planned, a backout plan (or rollback plan) provides steps to revert the system or application back to its previous state.
D. She should ensure a failover plan exists.
A failover plan is related to continuity of operations and disaster recovery, ensuring that if one system fails, another can take over. While this is crucial for maintaining availability, it doesn't specifically address the risk associated with a "change." It's more of a broader continuity plan.
Hint: CAB, Availability
18. What RADIUS alternative is commonly used for Cisco network gear and supports two-factor authentication?
a. RADIUS+
This is a made up term.
b. TACACS+
TACAS+ is the most version of TACAS (Terminal Access Controller Access-Control System)
c. XTACACS
XTACAS is an earlier version of TACAS and should be avoided
d. Kerberos
Kerberos is a network authentical protocol rather than a remote user authentication protocol. It is also a Microsoft product.
Hint: AAA Protocols, Kerberos
Questions 21–23 refer to the following scenario.
Hunter is the facilities manager for DataTech, a large data center management firm. He is evaluating the installation of a flood prevention system at one of DataTech’s facilities. The facility and contents are valued at $100 million. Installing the new flood prevention system would cost $10 million.
Hunter consulted with flood experts and determined that the facility lies within a 200-year flood plain and that, if a flood occurred, it would likely cause $20 million in damage to the facility.
Based on the information in this scenario, what is the exposure factor for the effect of a flood on DataTech’s data center?
2%
20%
The exposure factor is the percentage of the facility that risk managers expect will be damaged if a risk materializes. It is calculated by dividing the amount of damage by the asset value. In this case, that is $20 million in damage divided by the $100 million facility value, or 20%. The Exposure Factor (EF) represents the percentage of asset value that is expected to be lost due to a particular risk.
c. 100%
d. 200%
Based on the information in this scenario, what is the annualized rate of occurrence for a flood at DataTech’s data center?
a. 0.002
b. 0.005
c. 0.02
d. 0.05
B. The annualized rate of occurrence is the number of times each year that risk analysts expect a risk to happen in any given year. In this case, the analysts expect floods once every 200 years, or 0.005 times per year.
Based on the information in this scenario, what is the annualized loss expectancy for a flood at DataTech’s data center?
a. $40,000
b. $100,000
c. $400,000
d. $1,000,000
24. Which accounts are typically assessed during an account management assessment?
A random sample
Random samples are the second most likely choice.
Highly privileged accounts
The most frequent target of account management reviews are highly privileged accounts, as they create the greatest risk.
Recently generated accounts
Accounts that have existed for long periods of time
Accounts that have existed for a longer period of time are more likely to have a problem due to privilege creep than recently created accounts, but neither of these choices is likely unless there is a specific organizational reason to choose them.
25. What type of error occurs when a valid subject using a biometric authenticator is not authenticated?
A. A Type 1 error
Happens when a valid subject is not authenticated.
B. A Type 2 error
When an invalid subject is correctly authenticated (FAR).
C. A Type 3 error
Not a biometric error type.
D. A Type 4 error
Not a biometric error type.
Hint: Crossover Error
28. Which of the following statements is the least important to include in the his report?
The missing clickjacking x-frame options could be used to redirect input to a malicious site or frame.
This is a legitimate security concern that highlights the risk of not having clickjacking protections.
Cross-site scripting protections should be enabled, but aren't
Cross-site scripting (XSS) is a significant vulnerability in web applications. This statement emphasizes the need for such protections.
Inode information leakage from a Linux system is a critical vulnerability allowing direct access to the filesystem using node references.
Inode leakage can be a risk, but the statement exaggerates its impact. Leaking inode numbers doesn't directly grant access to the filesystem.
The server is a Linux server.
Knowing what you are working with is always important.
Hint: Threats
29. George is assisting a prosecutor with a case against a hacker who attempted to break into the computer systems at George’s company. He provides system logs to the prosecutor for use as evidence, but the prosecutor insists that George testify in court about how he gathered the logs. What rule of evidence requires George’s testimony?
Testimonial evidence rule
There's no specific "testimonial evidence rule." Testimonial evidence is evidence obtained from a witness who testifies under oath. In essence, George would be providing testimonial evidence if he testifies about how he gathered the logs.
Parol evidence rule
This rule deals with written contracts and the introduction of outside or additional evidence to contradict or add to the terms of a written agreement. It's not relevant to the scenario given.
Best evidence rule
This rule states that if a document is central to a party's argument, the original document must be produced unless there are acceptable reasons for its absence. In this case, while it might seem relevant given that the logs are a form of document, the main focus is not on the authenticity of the original logs but on the method of their collection.
Hearsay rule
In legal terms, hearsay isn't confined solely to human utterances. Machines or systems can also produce "statements" in forms such as logs, readouts, or printouts. While these logs often don't detail events explicitly, they can still be deemed hearsay when presented as evidence to verify the accuracy of their content. In this context, George's review of the logs equates to him "hearing" the computer's record of the alleged crime.
Hint: Evidence
31. Which one of the following malware types uses built-in propagation mechanisms that exploit system vulnerabilities to spread?
A. Trojan horse
B. Worm
C. Logic bomb
D. Virus
Hint: https://edu.water.house/link/59#bkmrk-worms
Meena wants to ensure that her supply chain risks are well managed. Which of the following is not a common practice she should include in her supply chain risk management (SCRM) plan?
A. Use contractual controls such as insurance and liability limitations where appropriate.
B. Sole source to provide vendor stability.
C. Ensure multiple suppliers exist for critical components.
D. Validate the financial stability of potential suppliers.
Hint: https://edu.water.house/link/8#bkmrk-supply-chain-evaluat
Using the following table and your knowledge of the auditing process, answer questions 38–40.
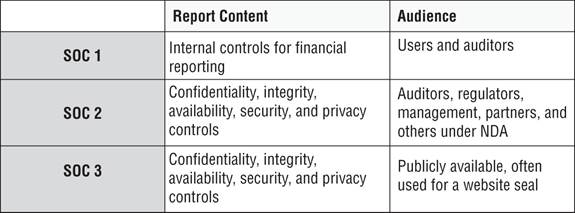
39. Susan wants to ensure that the audit report that her organization requested includes input from an external auditor. What type of report should she request?
a. SOC 2, Type 1
Type 1 Provides an opinion on management's control description and its design. It's a snapshot, reflecting a specific moment in time. Mainly a documentation review.
b. SOC 3, Type 1
SOC 3 does not have types.
c. SOC 2, Type 2
A SOC 2, Type 2 report includes information about a data center’s security, availability, processing integrity, confidentiality, and privacy, and includes an auditor’s opinion on the operational effectiveness of the controls.
d. SOC 3, Type 2
SOC 3 does not have types.
Hint: SOC
42. Bell-LaPadula is an example of what type of access control model?
DAC
Under DAC, access to resources is at the discretion of the user (typically the resource owner). In this model, permissions are given to users based on their identity or based on some criteria that categorize them, such as group membership.
RBAC
In RBAC, access to resources is determined by the roles assigned to users. Users are assigned roles, and roles have access rights and permissions associated with them.
MAC
In MAC, security labels (such as classified, secret, top secret, etc.) are assigned to objects and security clearances to subjects (users). Access decisions are made based on these labels and clearances.
ABAC
ABAC uses attributes, which can be related to the user, resource, or environment, to determine access. Policies are written using these attributes, which are then used to evaluate and decide whether access should be granted or denied.
Hint: MAC
45. Which one of the following techniques can an attacker use to exploit a TOC/TOU vulnerability?
A. File locking
Countermeasure
B. Exception handling
Countermeasure
C. Algorithmic complexity
Could be used as a complexity tool to exploit a time of change/time of use (TOC/TOU) condition. By carrying the workload of the CPU, attackers may exploit the amount of time required to process requests and use that variance to effectively schedule the exploit's succession.
D. Concurrency control
Countermeasure
Hint: TOCTTOU
58. Susan has discovered that the smart card-based locks used to keep the facility she works at secure are not effective because staff members are propping the doors open. She places signs on the doors reminding staff that leaving the door open creates a security issue, and adds alarms that will sound if the doors are left open for more than five minutes. What type of controls has she put into place?
a. Physical
While the alarm is a physical control, the signs she posted are not.
b. Administrative
This would be an option if the only placed the signs.
c. Compensation
However, if you interpret the alarms as being introduced to compensate for the ineffectiveness of the smart card locks due to human behavior (propping doors open), then you could make a case for c. Compensation. It's not the best definition, but the best option here.
d. Recovery
Nothing needs recovery here.
Hint: https://edu.water.house/link/41#bkmrk-types-of-security-co
62. As part of hiring a new employee, Kathleen’s identity management team creates a new user object and ensures that the user object is available in the directories and systems where it is needed. What is this process called?
a. Registration
Registration occurs when users are enrolled in a biometric system.
b. Provisioning
Provisioning includes the creation, maintenance, and removal of user objects from applications, systems, and directories.
c. Population
population and authenticator loading are not common industry terms.
d. Authenticator loading
population and authenticator loading are not common industry terms.
71. During which phase of the incident response would an organization determine whether is it required to notify law enforcements or other regulators of the incident?
Detection
Tools: Monitoring tools, IPS, Firewalls. Who gets Notified: Management and/or help desk
Recovery
Objective: Return to normal operations. Decision Maker: Management
Remediation
Focus: Address the root cause
Reporting
Who to Report: Stakeholders (customers, vendors, law enforcement)
Hint: NIST 800-61
73. Michelle is in charge of her organization’s mobile device management efforts and handles lost and stolen devices. Which of the following recommendations will provide the most assurance to her organization that data will not be lost if a device is stolen?
A. Mandatory passcodes and application management
Provides some assurance, but might not be the most comprehensive protection.
B. Full device encryption and mandatory passcodes
This provides a dual-layer protection. Both unauthorized access and unauthorized data extraction are dealt with.
C. Remote wipe and GPS tracking
This provides some assurance especially with the remote wipe feature, but if the thief is quick enough to disable the device's network connection, the remote wipe command might not be received.
D. Enabling GPS tracking and full device encryption
The combination here focuses on recovery (GPS tracking) and data protection (encryption), but lacks an immediate barrier to unauthorized access like a passcode.
Hint:
74 - if you have time
75. The large business that Jack works for has been using noncentralized logging for years. They have recently started to implement centralized logging, however, and as they reviewed logs they discovered a breach that appeared to have involved a malicious insider. Use this scenario to answer questions 75 through 77 about logging environments.
When the breach was discovered and the logs were reviewed, it was discovered that the attacker had purged the logs on the system that they compromised. How can this be prevented in the future?
a. Encrypt local logs
Encryption does not prevent log deletion or alteration, it merely protects the data from being read.
b. Require administrative access to change logs
Partially. While it's a good practice to require administrative access to change logs, it's not a foolproof measure against log tampering or deletion, especially if the attacker is an admin.
c. Enable log rotation
Log rotation involves creating new log files at regular intervals and archiving or deleting old log files. While this can ensure efficient log management and prevent storage issues, it doesn't specifically prevent an attacker from deleting or altering logs.
d. Send logs to a bastion host
This is the most effective option among the provided choices to prevent the issue in the scenario. Even if local logs are tampered with or deleted, a copy remains secure on the bastion host.
Hint: https://edu.water.house/link/35#bkmrk-bastion-host
76. if you have time
77. How can Jack best ensure accountability for actions taken on systems in his environment?
a. Log review and require digital signatures for each log.
Log review can be useful when identifying issues, but digital signatures are not a typical part of a logging environment.
b. Require authentication for all actions taken and capture logs centrally.
Requiring authentication can help provide accountability by ensuring that any action taken can be tracked back to a specific user. Storing logs centrally ensures that users can’t erase the evidence of actions that they have taken.
c. Log the use of administrative credentials and encrypt log data in transit.
Logging the use of administrative credentials helps for those users but won’t cover all users, and encrypting the logs doesn’t help with accountability.
d. Authorization helps, but being able to specifically identify users through authentication is more important.
Hint: AuthN vs AuthZ, Log Files
78. Ed's organization has 5 IP addresses allocated to them by their ISP but needs to connect more than 100 computers and network devices to the internet. What technology can he use to connect his entire network via the limited set of IP addresses he can use?
A. IPsec
IPsec (Internet Protocol Security) is a suite of protocols used for securing Internet Protocol (IP) communications by authenticating and encrypting each IP packet in a data stream. While IPsec is important for securing communications, it doesn't help in allowing multiple devices to share a single IP address.
B. PAT
PAT, often known as NAT overloading, is a feature that enables multiple devices on a local network to be mapped to a single public IP address. It works by differentiating devices based on the source port number. This means that multiple devices can have the same private IP address, but as long as they use a different source port, they can share the same public IP address. This option allows multiple devices in a private network to access the internet using a limited set of public IP addresses, making it the right solution for Ed's organization's situation.
C. SDN
SDN is a networking approach that allows network administrators to programmatically initialize, control, change, and manage network behavior dynamically via open interfaces and abstraction of lower-level functionality. While SDN offers many advantages for network management, it isn't the solution for sharing a limited number of IP addresses among multiple devices.
D. IPX
IPX is a networking protocol primarily used in Novell NetWare environments. It is not used for connecting devices to the modern internet, which primarily uses the IP protocol. Moreover, IPX does not offer a solution for the problem Ed's organization faces.
Hint: To be added
87. Ben is working on integrating a federated identity management system and needs to exchange authentication and authorization information for browser-based single sign-on. What technology is his best option?
A. HTML
Just used for web pages
B. XACML
XACML is for access control
C. SAML
Best choice for providing AuthN and AuthZ information, particularly for browser based SSO.
D. SPML
SMPL is for providing and managing user access.
Hint: https://edu.water.house/link/67#bkmrk-common-standards
89. What three types of interfaces are typically tested during software testing?
What three types of interfaces are typically tested during software testing?
Network, physical, and application interfaces
Network interfaces are not typically tested.
APIs, UIs, and physical interfaces
Application programming interfaces (APIs), user interfaces (UIs), and physical interfaces are all tested during the software testing process.
Network interfaces, APIs, and UIs
Network interfaces are not typically tested.
Application, programmatic, and user interfaces.
Programmatic interfaces is another term for APIs, so it's mentioned twice.
Hint: Interface Testing
90. Amanda wants to monitor her LDAP servers to identify which types of queries are causing problems. What type of monitoring should she use if she wants to be able to use the production servers and actual traffic for her testing?
A. Active
This type of monitoring involves sending test traffic or synthetic queries to the server. It can interfere with regular operations and might not provide an accurate picture of real-world problems. This is not ideal for Amanda's scenario since she wants to use actual traffic.
B. Real-time
Real-time monitoring provides information about events as they happen. While this might sound like the correct choice, real-time monitoring does not necessarily imply that it is non-intrusive or passive. It just means the data is analyzed and presented immediately.
C. Passive
In passive monitoring, the system simply listens to and records network traffic without interfering or actively sending requests. This approach allows for the monitoring of real traffic without the risk of disrupting operations.
D. Replay
This means capturing traffic and then replaying it later, potentially in a lab environment or against a test server. Since Amanda wants to use the production servers and actual traffic for her testing, this option doesn't align with her needs.
https://edu.water.house/link/45#bkmrk-website-monitoring
96. Elle's organization has had to shift to remove work. Each staff member needs access to specific applications, and due to the quick shift, staff members are working from systems that may be home systems or borrowed laptops. What is the best option for remote access in a situation like the one that Elle is facing?
An IPSec VPN
They require a client to be set up on the end-user's device, which might not always be feasible for personal or borrowed laptops. Also, the underlying system's security posture isn't considered, potentially allowing compromised devices to connect.
Dedicated fiber connection to each remote work location
Highly impractical and extremely costly to implement. This approach would mean physically laying down fiber optic cables to each employee's house, which isn't feasible.
An HTML5-based VPN
These solutions operate clientlessly through web browsers, making them more adaptable for various devices, including personal or borrowed systems. It provides secure remote access without needing to install additional software.
Use of remote desktop to connect to an existing workstation at the company's office building.
RDP does not perform any control checks.
Hint: Think like a manager, come back if you have time
97. Come back if you have time
106. Which one of the following background checks is not normally performed during normal pre-hire activities?
A. Credit check
B. Reference verification
C. Criminal records check
D. Medical records check
109. Tommy handles access control requests for his organization. A user approaches him and explains that he needs access to the human resources database to complete a headcount analysis requested by the CFO. What has the user demonstrated successfully to Tommy?
A. Clearance
B. Separation of duties
C. Need to know
D. Isolation
110. Kathleen wants to set up a service to provide information about her organization’s users and services using a central, open, vendor-neutral, standards-based system that can be easily queried. Which of the following technologies is her best choice?
RADIUS
Authentication protocol, not directory.
LDAP
Is an open, industry-standard, and vendor-natural protocol for directory services
Kerberos
Authentication protocol, not directory.
Active Directory
Microsoft proprietary
https://edu.water.house/link/30#bkmrk-common-tcp%2Fudp-ports-1 , RADIUS,
112. Alice would like to add another object to a security model and grant herself rights to that object. Which one of the rules in the Take-Grant protection model would allow her to complete this operation?
A. Take rule
Allows a subject to take rights over an object
B. Grant rule
Allows a subject to grant rights to an object
C. Create rule
Allows a subject to create new rights
D. Remove rule
Allows a subject to remove rights it has
https://edu.water.house/link/13#bkmrk-take-grant
113. come back maybe
115. Which ITU-T standard should Alex expect to see in use when he uses his smart card to provide a certificate to an upstream authentication service?
A. X.500
B. SPML
C. X.509
D. SAML
Hint: https://edu.water.house/link/67#bkmrk-certificate-based-au
119. What two important factors does accountability for access control rely on?
A. Identification and authorization
B. Authentication and authorization
C. Identification and authentication
D. Accountability and authentication
Hint: https://edu.water.house/books/cissp-study-guide/page/identity-access-management#bkmrk-authorization
120. What part of the CIA triad does a checksum support
Availability
Integrity
Confidentiality
Authenticity
Hint: https://edu.water.house/link/3#bkmrk-page-title



